9 October 1997
Source:
http://www.ispo.cec.be/eif/policy/97503annex.html
| ANNEX I
Digital Signature |
• Usage
Digital signatures can help to prove the authenticity and integrity of data. A secure digital signature system will consist of two parts: on one hand a method to sign a document in a "not forgery" way and on the other hand a method to verify that the signature was generated by whom it represents. The authentication protocols can be based on public key encryption systems (using asymmetric cryptographic algorithms). For a detailed description of symmetric and asymmetric cryptographic algorithms see Annex II.
A digital signature is a string of data created by using a private key. A public key can be used to verify that the signature was effectively generated by using the corresponding private key. It should be created in such a manner that it is impossible to create a valid signature without knowing the private key. The authentication of strings of data is a process where the receiver of, for instance, a digital message can be assured about the origin of a message.
The string of data can also contain pseudonyms or names to be used to read the identity of the sender. In addition the string can carry a timestamp to testify that a message (or document) existed at the stated time.
Digital signatures can also be used to certify that a certain public key belongs to a certain person.
• Creation
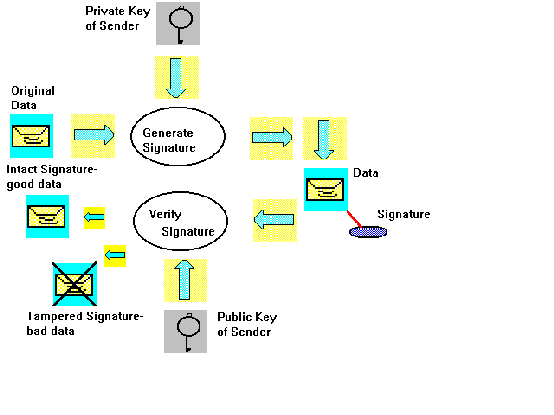
In order to create a digital signature, two steps are necessary. First the sender computes with the help of software a digest of the data containing its essential characteristics (so-called "hash function": a sort of short version of the data). Unlike the procedure when encrypting data to preserve confidentiality, he encrypts the digest - together with additional data, including place and time of the signature - with his private key and not with the public key of the receiver. Thus, the key does not serve to encrypt the plaintext itself, but only to encrypt the digital signature that is annexed to the readable data [for a detailed description see Annex II].
Thus, the recipient of the data can now be sure that the transmitted data has not been altered and that the public and private key of the sender are a complementary key-pair.

• Hash functions
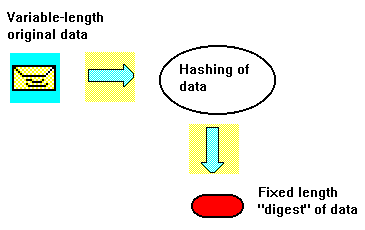
Hash functions are used to compute a data digest when making digital signatures. These functions map the data to fixed sized hash values in such a way that it would be extremely difficult to come up with a string of data that would match these particular hash values. The idea is based on the fact that a message digest represents concisely the ‘original’ data from which it was computed. It could be considered as a digital fingerprint of the ‘larger’ data string. As hash functions are a lot faster than the all data signing functions it is a lot more efficient to compute a digital signature by using the digest than using all the data.
To use the hash functions for digital authentication they must have certain properties to make them secure enough for cryptographic usage. It must be excluded that a data string can be found that hashes to a given value and that two distinct data strings hash to the same values. Cryptographic hash algorithms produce hash values of at least 128 bits.
To break into a digital signature system attacks may or will be directed at the mathematical string used by the digital signature system or the hash function used to make the data digest. In order to obtain an adequate security level it seems necessary to choose a digital signature system and a hash function that are evenly matched in difficulty to break. Attacks will take place on the weakest of both components. Therefore long modules and hash functions producing longer data digests should be used.
Examples: Message Digest-algorithms MD2, MD5 (128-bit values), Secure Hash Standards/Algorithms (SHS/SHA) and RIPEM 160.
|
• Overview of the different processing steps of a digital signature:
• Open network security
As the TCP/IP (Transmission Control Protocol/Internet Protocol) was not designed to offer secure communication services over the Internet (the Internet Protocol version 6 currently under development, will include some security oriented features) additional security technologies are needed to tackle the increasing security concerns.
Secure electronic infrastructures are mainly based on SSL (Secure Sockets Layers), SET (Secure Electronic Transactions) and S/MIME (Secure Multipurpose Internet Mail Extensions). These industry-standard protocols provide the basis for a wide variety of security services (digital signatures, message integrity verification, authentication and encryption).
The most commonly used browsers (Netscape Navigator and Microsoft Internet
Explorer) exploit most of these possibilities together with the use of
SSL-capable servers from the leading vendors. Additional security features
requested by specific computer applications can be incorporated by other
API (Application Program Interface), Java scripts, Java-applets, Visual Basic,
C/C++ or other programming languages.
| ANNEX
II
Symmetric and asymmetric encryption |
• What is encryption?
Encryption is the transformation of data into a form unreadable by anyone without a decryption key. Cryptographic algorithms are used to transform plaintext data into encrypted data. The act of transforming the information is called The process of transforming data back into plaintext is called decryption. The purpose of encryption is to ensure confidentiality by keeping the information hidden from anyone for whom it is not intended, even for those who can see the encrypted data. It addresses the data protection and privacy issues, including data integrity and confidentiality, and allows secure communication over insecure channels.
There are two basic types of encryption: symmetric and asymmetric.
• Symmetric (or secret key) encryption systems
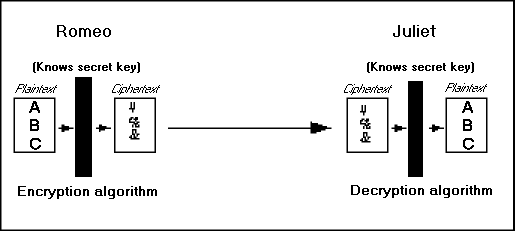
In symmetric encryption systems one key is used both to encrypt and decrypt data. To provide security for the information, the key needs to be kept as a secret between parties involved. Symmetric encryption is suitable for transforming large amounts of data since computations are performed rapidly. Management of the distribution and use of the secret key is critical as the key is vulnerable in transit to the other party.
Examples of symmetric algorithms: the Data Encryption Standard (DES) algorithm, Fast Encryption Algorithm (FEAL), International Data Encryption Algorithm (IDEA), RC4 and RC5, Secure and Fast Encryption Routine (SAFER)
• Asymmetric (public key) encryption systems
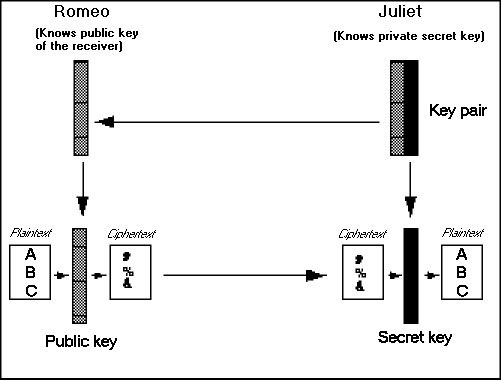
Asymmetric encryption systems are based on the use of two keys in a single cryptographic operation: one key to encrypt, another key to decrypt. The encryption key is called the public key, the decryption key is called the private key. These keys are related in a complex way. A message encrypted with a particular public key can only be decrypted by using the corresponding private key; like data encrypted with a private key can only be decrypted by using the corresponding public key.
Examples: the RSA public key algorithm, Diffie-Hellmann.
The private key should be stored securely in a protected medium such as a smartcard, a portable computer or a smartdisk. The most common hardware solution will probably be the smartcard as the private key cannot be separated from the card and is difficult to copy. In addition the use of smartcards can be protected, for example using a PIN-number or a finger print matching technique. The public key, as the name already indicates, is published and accessible to everyone. Therefore asymmetric algorithms are often called public-key algorithms.
Example: If someone, say Romeo, wants to send a confidential message using a public-key mechanism to someone else, say Juliet, he needs to encrypt the plaintext, probably something like "I love you", with her public key. He could send the encrypted message safely over an unsecured network as only Juliet can decrypt the ciphertext with her private key. Thus, public-key cryptographic systems open the use of encryption to huge user groups.
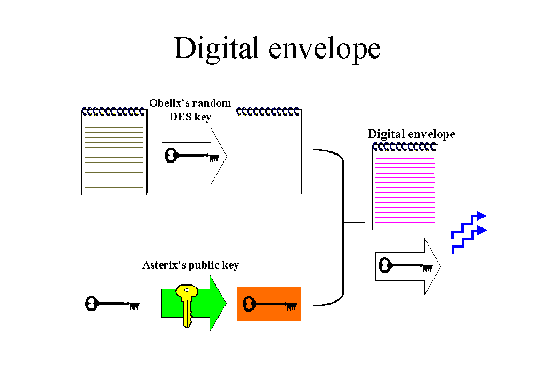
• Digital envelope
A major disadvantage of asymmetric algorithms is that they are significantly slower than symmetric algorithms. This disadvantage can be overcome by using a combination of both algorithms in order to create a so-called digital envelope.
The plaintext is encrypted with a fast symmetric algorithm using a relatively short but nevertheless secure key. Additional security is provided if the key is only used once (message or session key) and irrecoverably destroyed as soon as the communication ends. Only this key needs to be encrypted with the public key of the receiver. For example, Romeo sends both ciphertext and encrypted session key to Juliet. By using her private key to decrypt the session key Juliet is able to decrypt the full ciphertext.
Example: Pretty Good Privacy (PGP) uses IDEA and RSA
• Systems security
In theory, some keys could be found on the basis of systematic trials ("brute-force" attacks). However the length of the key can be determined in such a way that the code could not be cracked within a practically feasible time period.
In an asymmetric, or public key, cryptographic system, keys with a length of 1,024 bits are considered to be secure at present. This corresponds to a string of more than 300 digits. Using today's computer technology, such keys would take centuries to crack. In a symmetric system like DES or IDEA, keys of 56 to 128 bits provide similar protection as a 1,024-bit public key.
Encryption is also useful for electronically stored information as it can not be excluded that unauthorized persons like computer hackers gain access to data. As some kind of data needs to be stored securely for long time periods, effective crypto-systems are necessary, using appropriate key lengths.
Such storage keys have the same importance as the stored data. For this reason it could be useful to make sure that the key can be recovered in case of loss, for instance if the owner of the key dies, an employee leaves the company with the key, etc. For secure communication such a key recovery mechanism is not necessary. If a message is lost during the transmission, the simplest way is to send it again, encrypted with a new key.
There is no general theory to design absolute secure systems or to assess with scientific reliability their degree of security. Hackers will try to find vulnerabilities in systems to avoid costly brute-force attacks (e.g. people that disclose information, failure in the algorithm, electromagnetic radiation emanating from computer screen, etc.). Given enough resources, time and skills, almost any system can be broken. The economic logic behind security is to make a system more difficult and expensive to break than the effort would be worth to hackers. As a result, there are different levels of security precautions, from simple passwords to very strong encryption. As any system is only as secure as its weakest link, systems security therefore needs to be continually analysed and adapted.
• Steganography
Data can be hidden using steganography. These methods reduce the chance of certain data being detected. If that data is also encrypted it gives an additional layer of security. The word steganography literally means "covered writing". It includes a vast array of methods of secret communications that conceal the very existence of the hidden data. Among these methods are invisible inks, microdots, character arrangement (other than the cryptographic methods of permutation and substitution), covert channels and spread-spectrum communications.
In contrast to cryptography, where the "enemy" can detect, intercept and
modify messages without being able to violate certain security premises
guaranteed by a cryptosystem, the goal of steganography is to hide the wanted
secret data in other data in such a way that it doesn’t allow anybody
to even detect that there is some hidden data present. It is not intended
to replace encryption systems but it provides a supplementary difficulty
for data to be cracked. These methods are no longer limited to embed text
in images but can also be used for other media like voice, video etc.
| ANNEX
III
Key escrow / key recovery |
• Definition
Key escrow and key recovery systems are encryption systems providing a backup decryption capability allowing authorised institutions under certain conditions to decrypt data using information supplied by one or more Trusted Third Parties (TTPs - trusted means trusted by both sides, the user and the government agency).
• Key escrow
In a key escrow system a copy of any secret key generated is deposited with an authorised TTP. The key could also be split into two or more parts that are deposited with different TTPs. In accordance with national law TTPs would have to hand over the key to the competent government agencies.
Once a copy of a private key is handed over to a third party, this key can no longer be regarded as fully secret. All communications and stored data encrypted with this key could eventually be decrypted.
• Key recovery
Within a key recovery system the private key would not be escrowed right from the beginning. The encryption system would allow authorised organisations, such as licensed TTPs, to rebuild the key on request.
Once the key is rebuilt through a key recovery system the result is the same as if the key would have been escrowed. Therefore a key recovery system would only make a difference if exclusively session keys (a key which is only used once and normally irrecoverably destroyed as soon as the communication ends) were recoverable. But even in such a key recovery system TTPs would theoretically be able to decrypt all session keys.
Technically both schemes allow access to all encrypted information. Consequently
the difference depends essentially on the institutional arrangements set
by national law.
| ANNEX
IV
Commission initiatives |
• PROJECTS IN THE INFORMATION TECHNOLOGY PROGRAM
20563 E2S(SW): The goal of the project is to contribute to the growth of Electronic Commerce on the Internet by developing, testing and installing end-to-end security mechanisms for commercial transactions using the Internet. The plan is to deliver a professional infrastructure that is attractive to businesses and consumers, enabling the economic growth promised by the "information society".
22005 WIRE(SW): The overall goal of the WIRE project is to make it possible for organisations to deploy Secure Enterprise Webs. Today, many organizations have set up Web servers for non strategic IT applications to deliver public information to the market at a low cost compared to advertisement in other media. This current WEB technology is successful when data is public (access control is not required), small (less than thousands of pages) and simple (text, numbers, built-in .gif images). These conditions are too restrictive for professional applications. Commercial transactions require strong support for user authentication and access control.
24103 FACTMERCHANT(TBP): The pilot will demonstrate the integration of secure billing, e-mail and EDI on a platform, which provides comprehensive access to business information. This will include news and rates, world-wide market and broker research, and financial and credit analysis. The pilot will be run over Internet for access for both SMEs and larger organizations. The pilot will use knowledge-based systems technology for search, public-key cryptography and digital signatures for confidentiality, authentication, integration and non-repudiation.
22803 ICX (TBP): A business driven European User Group, to be known as the International Commerce eXchange (ICX), is proposed. ICX will be a European Forum for the discussion, identification and subsequent resolution of security issues in the electronic commerce arena.
9801 WEBCORE(SW): The W3C is an international industry consortium which seeks to promote standards for the evolution of the Web and interoperability between World Wide Web (WWW) products by producing specifications and reference software. Although W3C is funded by industrial members, it is vendor-neutral, and its products are freely available to all. In early 1996, W3C identified digital signature to be one of the major market drivers for Web security and launched the so called Digital Signature Initiative.
• PROJECTS IN "STANDARDISATION AND THE INFORMATION SOCIETY"
C-SET (Interoperable Chip-secured Electronic Transaction)
As the need for Electronic Commerce emerges, Visa and MasterCard have developed the SET (Secure Electronic Transaction) protocol to secure payment transactions on open networks by software. Worldwide card schemes will mostly apply to SET payment regulations according to which the merchant is not paid if the cardholder repudiates the transaction. Some regional card schemes, such as CB and Banksys, enjoy a high level of security in domestic face-to-face payments thanks to the use of the micro-circuit card. They wish to enhance SET so as to support the use of microcircuit cards, thus providing the additional security needed to fully guarantee payments over open networks.
• PROJECTS IN THE ACTS PROGRAM
AC026 SEMPER
Background Networked information systems are experiencing a tremendous growth in terms of users and traffic as well as publicity. The dominating application is the Internet- based World Wide Web (WWW), with its potential of 3 million connected individual computers and an order of magnitude more actual users. WWW is still dominated by free-of-charge information systems, but this is expected to change dramatically in the near future. WWW will be used for all sorts of electronic commerce and trade, like online offering, ordering, payment, and delivery of services, information, and exchange of business documents. The same development can be expected for the IBC networks and "Information Highways."
• PROJECTS ON SECURITY OF TELECOMMUNICATIONS AND INFORMATION SYSTEMS
Interworking public key certification infrastructure for Europe (ICE-TEL)
The aim of ICE-TEL is to increase the trustworthiness of the Internet as used by industrial and academic research. The project will support security-enhanced applications by providing users with public key certification services in several European countries. It will also incorporate a security infrastructure and user platform to adapt and integrate the necessary tools and toolkits for incorporating public key-based security into applications as WWW, e-mail, electronic directories and multimedia conferencing. The three project applications selected for tools validation will involve secure communication between national computer emergency response teams and other network support groups, public administrations and protected access to electronic directories.
Multimedia European Research conference integration (MERCI)
The purpose of MERCI is to support joint research and technological development by deploying better tools for multimedia collaboration in Europe. Existing toolsets will be made easier for untrained personnel to use, with better quality audio, video and shared workspace facilities, and better support for multimedia applications in conferences. Distributed measurement, monitoring and control will be another important feature, as will improve privacy in conferencing. Verification, both within MERCI and other telematics projects, will include regular research seminars and industrial trials with commercial organisations.
Directory based EDI certificate access and management (DEDICA)
DEDICA plans to offer EU electronic data interchange (EDI) operators in sectors like banking, data security arrangements for them to network with so-called open system and distributed services, like electronic mail, which at present rely on different security standards. The proposal will involve making the certification infrastructure now employed for authenticating electronic messages in open systems compatible with EDI certification. A shared infrastructure will result in economies of scale for service providers, satisfy the global service needs of EDI operators and give e-mail users secure access to EDI.
Trustworthy health telematics (Trusthealth)
In TRUSTHEALTH, a network of bona fide national organisations working in health care computerisation will show how openly-linked European telematics systems can employ modern data security measures. Based on a 1994 EU user survey, the project will adopt coded digital signature techniques to meet legal requirements and sustain public confidence in information security. Among numerous urgent application areas are drug prescriptions, electronically exchanged laboratory data and health center invoicing. Network partners will collaborate in delivering security techniques for subsequent transfer to permanent health service operations.
Implementing secure healthcare telematics applications in Europe (ISHTAR)
Tight precautions to protect data in telematics-supported health services in Europe are the central concern of ISHTAR. The project will set up an expert group to advise and support the Commission and other personnel involved in security-sensitive health telematics projects. Existing guidelines on protection will be reinforced and products and services tested. The usefulness of telematics in handling the technicalities of data security will also be demonstrated. The project will launch publicity to heighten awareness of protection issues and also consider their legal and social implications.
Data protection in the European Union (DAPRO)
The purpose of DAPRO is to structure and demonstrate the content of the July 1995 EU Data Protection Directive as a basis for legal regulation of expanding telematics applications, and to clarify its relation to Member State law in this field. Both private and public sectors need such information, including case law, comments, data protection agency addresses, glossary and user guides, which will be published in an electronic system with a hypermedia interface. A publishing company will be responsible for implementing and marketing the system which will facilitate the extension of data protection law to other Member States.
• PROJECTS IN THE EUROPEAN TRUSTED SERVICES PROGRAM (ETS)
Oparate
The aim of the project is to investigate operational and architectural aspects of TTP service provision: how a TTP should be organized and operated in order to provide TTP services effectively; how different TTP systems may be combined or made to interwork together, and in particular: how an ES/TTP network may be extended to provide confidentiality/key recovery services; how interworking may be achieved between heterogeneous TTP networks.
Eurotrust
Goal of the project is to operate a pilot Certification Authority (CA)/ Trusted Third Party service.
Oscar
The emphasis of the pilot is on certification in support of European Internal Market: how is it possible to certify business of users, to support secure messaging and any other communications services inside a country and across Europe.
Krisis
The project will try to define a key recovery scheme accepted by the commercial sector that also provides appropriate means for law enforcement.
Mandate II
It uses a functionally Trusted Third Party to provide the confidence needed for a new electronic financial negotiable instrument. Designed as a generic solution to electronic negotiability, MANDATE will ultimately be built on tamper-resistant hardware, known as a DOC-carrier, and using public-key cryptography to provide the security required.
Aequitas
The study will establish an experimental TTP, which will act as a service of certification for a group of lawyers, judges and prosecutors in their daily practice.
Euromed-ETS
The first objective of this project is using the experts' experiences and findings to identify, define and verify operational, technical, regulatory and legal aspects of the TTPs for telemedical applications over the WWW. The second objective is to implement the above adjusted findings in EUROMED's configuration, which is a telemedical application over the WWW, with regards to effectiveness, economics and acceptability.
Eagle
EAGLE will study commercial, technical and regulatory aspects of TTPs.
| ANNEX V
World Wide Web addresses |
Additional information on security and trust in electronic communications and related aspects can be found on the following Commission World Wide Web servers:
http://europa.eu.int/en/comm/dg13/13home.htm
http://europa.eu.int/comm/dg15/index.htm